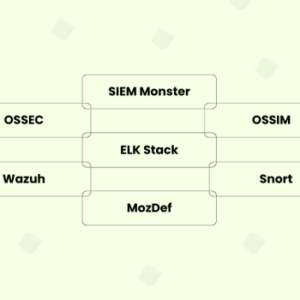
SIEM software open source offers a compelling alternative to commercial solutions, providing robust security information and event management capabilities without […]
Tag: Cybersecurity
Government Software Engineer Jobs A Comprehensive Guide
Government software engineer jobs are increasingly in demand, offering rewarding careers with significant impact. This guide explores the current job […]
Bullet-Proof Software A Comprehensive Guide
Bullet-proof software represents the pinnacle of secure application design, going beyond typical security measures to offer unparalleled protection against threats. […]
US Treasury Hacked by China A Deep Dive
US Treasury hacked by China? The headline alone sends shivers down the spine, conjuring images of digital espionage and economic […]
Attack Shark Software A Deep Dive
Attack Shark Software: the name alone evokes a sense of danger and intrigue. This exploration delves into the multifaceted interpretations […]
Attack Shark X3 Software A Comprehensive Analysis
Attack Shark X3 software, with its provocative name, immediately sparks curiosity. This analysis delves into the potential functionalities, target audiences, […]
Attack Shark Mouse Software A Deep Dive
Attack Shark Mouse Software sets the stage for an exploration of a hypothetical software concept, blending aggressive naming with intriguing […]