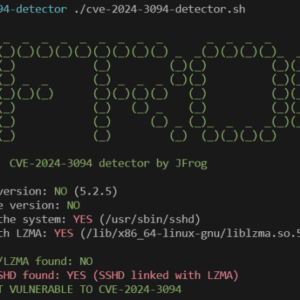
Xz backdoor everything you need to know – XZ Backdoor: Everything You Need to Know. Think your system’s impenetrable? Think […]
Category: Cybersecurity
Jia Tan XZ Backdoor Unveiling the Mystery
Jia Tan XZ backdoor – the phrase itself whispers intrigue. What secrets does it hold? Is it a hidden pathway […]
P4x North Korea Internet Hacker Identity Reveal
P4x North Korea internet hacker identity reveal: The shadowy world of North Korean cyber warfare just got a little less […]
Infrared Laser Microphone Keystroke Surveillance
Infrared laser microphone keystroke surveillance: Imagine a world where the silent tap-tap-tap of your fingers on a keyboard isn’t so […]
USPS Scam Text Smishing Triad Decoding the Deception
USPS scam text smishing triad: Ever gotten a text about a missed package? Think twice before clicking! These sneaky scams […]
Microsoft Copilot Phishing Data Extraction
Microsoft Copilot phishing data extraction: It sounds like a sci-fi thriller, doesn’t it? But the reality is, this emerging technology, […]
HID Keycard Authentication Key Vulnerability Exposed
HID keycard authentication key vulnerability: Think your swipe card is secure? Think again. From seemingly innocuous office buildings to high-security […]